안녕하세요, 쯀리입니다.
오늘은 6강의 마지막 Network Policy에 대해 알아보겠습니다.

https://kubernetes.io/ko/docs/concepts/services-networking/network-policies/
네트워크 정책
IP 주소 또는 포트 수준(OSI 계층 3 또는 4)에서 트래픽 흐름을 제어하려는 경우, 네트워크 정책은 클러스터 내의 트래픽 흐름뿐만 아니라 파드와 외부 간의 규칙을 정의할 수 있도록 해준다. 클러
kubernetes.io
Network Policy
Kubernetes(K8s) 클러스터 내에서 포드(Pod) 간의 트래픽을 제어하기 위한 규칙 세트를 말합니다.
주요 개념
- 네임스페이스(Namespace): 네트워크 폴리시는 특정 네임스페이스 내에서만 적용돼요.
- 레이블(Label): 포드를 식별하기 위해 레이블을 사용해요. 네트워크 폴리시는 레이블을 기반으로 적용돼요.
- 인그레스(Ingress)와 이그레스(Egress): 인그레스는 포드로 들어오는 트래픽을, 이그레스는 포드에서 나가는 트래픽을 의미해요.
Quiz.
1. How many network policies do you see in the environment?
We have deployed few web applications, services and network policies. Inspect the environment.
controlplane ~ ➜ k get networkpolicy
NAME POD-SELECTOR AGE
payroll-policy name=payroll 4m35s
2. What is the name of the Network Policy? payroll-policy
3. Which pod is the Network Policy applied on? payroll
4. What type of traffic is this Network Policy configured to handle? ingress
controlplane ~ ➜ k describe networkpolicy payroll-policy
Name: payroll-policy
Namespace: default
Created on: 2024-07-28 11:25:23 +0000 UTC
Labels: <none>
Annotations: <none>
Spec:
PodSelector: name=payroll
Allowing ingress traffic:
To Port: 8080/TCP
From:
PodSelector: name=internal
Not affecting egress traffic
Policy Types: Ingress
5. What is the impact of the rule configured on this Network Policy?
Traffic from internal to Payroll pod is allowed
6. What is the impact of the rule configured on this Network Policy?
Internal pod can access port 8080 on Payroll POD
7. Access the UI of these applications using the link given above the terminal.

8. Perform a connectivity test using the User Interface in these Applications to access the payroll-service at port 8080.
controlplane ~ ➜ k get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
db-service ClusterIP 10.108.200.16 <none> 3306/TCP 44m
external-service NodePort 10.105.31.107 <none> 8080:30080/TCP 44m
internal-service NodePort 10.106.213.71 <none> 8080:30082/TCP 44m
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 106m
payroll-service NodePort 10.103.198.187 <none> 8080:30083/TCP 44m
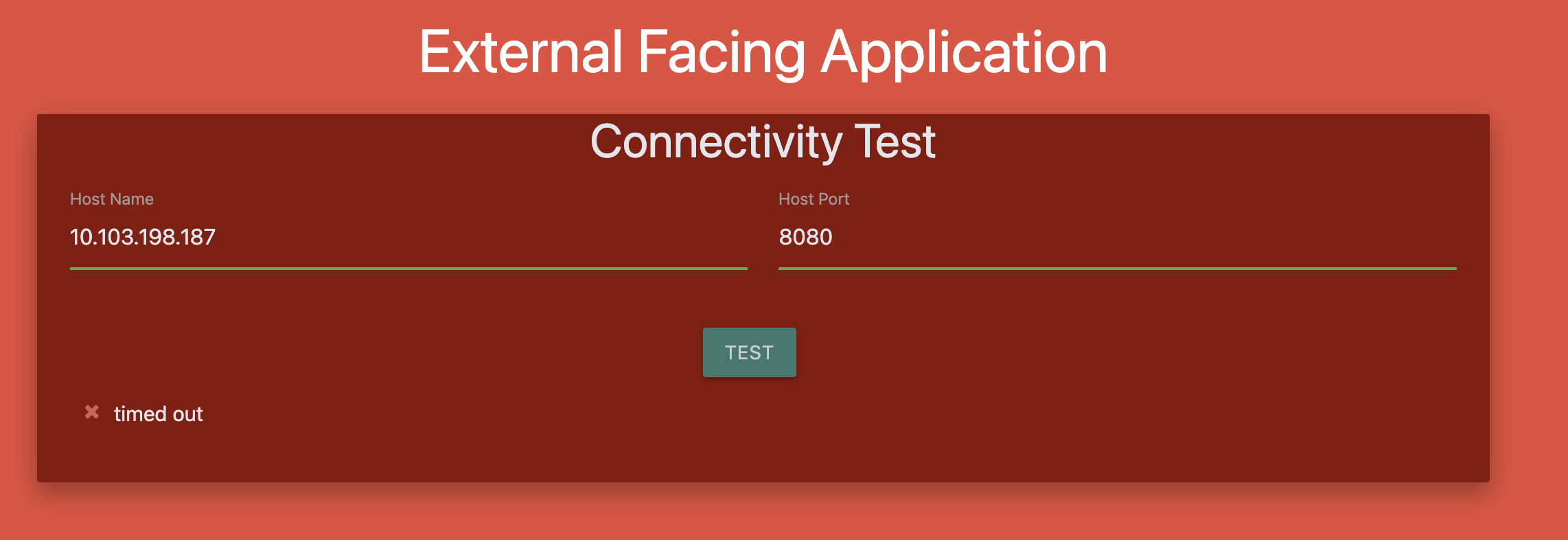
Internal Facing Application에서 접근가능합니다.
Only Internal application can access payroll service
9. Perform a connectivity test using the User Interface of the Internal Application to access the external-service at port 8080.

10. Create a network policy to allow traffic from the Internal application only to the payroll-service and db-service.
Use the spec given below. You might want to enable ingress traffic to the pod to test your rules in the UI.
Also, ensure that you allow egress traffic to DNS ports TCP and UDP (port 53) to enable DNS resolution from the internal pod.
Policy Name: internal-policy
Policy Type: Egress
Egress Allow: payroll
Payroll Port: 8080
Egress Allow: mysql
MySQL Port: 3306
-------------------------------
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
name: internal
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- ports:
- port: 53
protocol: UDP
- port: 53
protocol: TCPcontrolplane ~ ➜ k apply -f internal-policy.yaml
networkpolicy.networking.k8s.io/internal-policy created
controlplane ~ ➜ k get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 119m
controlplane ~ ➜ k get networkpolicy
NAME POD-SELECTOR AGE
internal-policy name=internal 8s오늘은 간단히 Network Policies에 관해 알아보았습니다.
네트워크 폴리시는 클러스터 내에서 보안을 강화하고, 특정 포드 간의 통신을 세밀하게 제어하는데 매우 유용해요.
네트워크 폴리시를 제대로 설정하면 클러스터의 보안성을 크게 향상시킬 수 있어요.
다음시간에는 7강에서 만나요!
참조
'IT 잡지식 > DevOps' 카테고리의 다른 글
| [CKA] KodeKloud - Storage Class (0) | 2024.07.29 |
|---|---|
| [CKA] KodeKloud - Persistent Volume Claims (0) | 2024.07.28 |
| [CKA] KodeKloud - Security Contexts (0) | 2024.07.24 |
| [CKA] KodeKloud - Image Security (0) | 2024.07.20 |
| [CKA] KodeKloud - Service Account (0) | 2024.07.20 |



